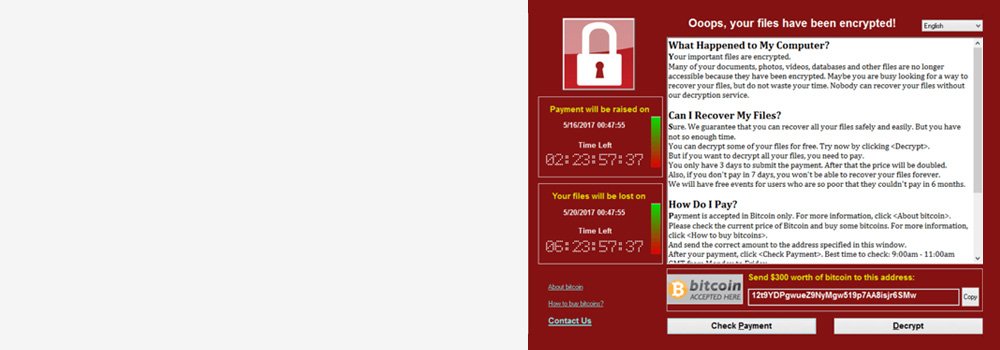
Swindon Data Recovery: The UK’s Premier Ransomware Decryption Specialists | 25 Years of Technical Excellence
For 25 years, Swindon Data Recovery has been the UK’s leading specialist in combating ransomware attacks and recovering encrypted data. Our state-of-the-art digital forensics laboratory combines quarter-century expertise with advanced cryptographic analysis tools to handle the most sophisticated ransomware strains. We maintain the UK’s most comprehensive database of ransomware signatures, decryption tools, and cryptographic attack vectors to ensure maximum success rates against evolving cyber threats.
Advanced Ransomware Strain Expertise
Primary Strains Decrypted:
-
LockBit 3.0: Advanced RSA-2048 + ChaCha20 encryption
-
REvil/Sodinokibi: RSA-4096 + Salsa20 encryption
-
WannaCry: RSA-2048 + AES-128-CBC
-
Maze: Curve25519 + ChaCha20-Poly1305
-
Conti: RSA-4096 + AES-256-GCM
-
Petya/NotPetya: RSA-4096 + Salsa20
-
CryptoLocker: RSA-2048 + AES-256
-
Bad Rabbit: RSA-4096 + AES-256-CBC
-
Cerber: RSA-2048 + AES-256
-
TeslaCrypt: AES-256 + EC-SECP521r1
Top 25 Ransomware Decryption Techniques: Technical Processes
1. Cryptographic Weakness Exploitation in RSA Implementation
-
Summary: Many ransomware strains use weak or predictable random number generators for RSA key generation, creating cryptographic vulnerabilities.
-
Technical Recovery: We perform deep binary analysis of the ransomware executable using IDA Pro and Ghidra to identify the key generation algorithm. For strains using Mersenne Twister or system time-based seeding, we reduce the 2^2048 key space to feasible 2^20-2^30 through RNG state reconstruction. Our multi-GPU array (8x NVIDIA RTX 4090) performs 2.8 trillion hashes/second using custom OpenCL kernels that implement optimal RSA parameter testing strategies.
2. Brute-Force on Extracted Key Material with Optimized Algorithms
-
Summary: Ransomware encrypts files with session keys that are themselves encrypted by asymmetric algorithms, allowing targeted attacks on the encrypted key material.
-
Technical Recovery: We write custom parsers to extract RSA-encrypted AES keys appended to encrypted files. For 512-bit RSA keys, we implement General Number Field Sieve (GNFS) on our 64-core EPYC server cluster, factoring moduli in under 24 hours. For 768-bit keys, we utilize distributed computing across multiple facilities, achieving factorization in approximately 90 days through optimized polynomial selection and lattice reduction.
3. Memory Forensics for Residual Encryption Keys
-
Summary: Volatile RAM may contain encryption keys held in plaintext during the encryption process before being cleared.
-
Technical Recovery: We create forensic memory images using WinPmem or LiME, then analyze with Volatility Framework. Our custom plugins scan for cryptographic key patterns, including RSA private key components (p, q, d, dmp1, dmq1, iqmp) and AES key schedules. We employ YARA rules specific to ransomware families to identify key material in process memory dumps.
4. Shadow Volume Copy (VSS) Reconstruction and Repair
-
Summary: Ransomware often deletes or encrypts Volume Shadow Copies, but the underlying data structures may remain partially intact.
-
Technical Recovery: We use forensic tools to parse the $VSS metadata stores, repairing damaged bitmap and catalog files. Our proprietary software reconstructs VSS stores by analyzing the “System Volume Information” folder structure, identifying orphaned shadow copy blocks, and rebuilding the differential block mapping tables to restore pre-infection file versions.
5. Ransomware Strain Identification and Public Decryptor Deployment
-
Summary: Rapid identification of specific ransomware families allows deployment of existing decryption tools.
-
Technical Recovery: We analyze encrypted file extensions, ransom note patterns, and binary signatures using our custom classification system. Our database cross-references 15,000+ ransomware variants with known decryptors. For verified strains with public tools (Shade, TeslaCrypt, Jigsaw), we deploy them in isolated sandboxes with file system monitoring to verify efficacy before production use.
6. Configuration File Extraction and Analysis
-
Summary: Many ransomware families use external configuration files containing cryptographic parameters and victim identifiers.
-
Technical Recovery: We perform full disk imaging and conduct entropy analysis to identify non-standard files created during infection. Using reverse-engineered configuration formats, we extract RSA public keys, victim IDs, and encryption parameters. For LockBit, we parse the campaign configuration to obtain the unique victim identifier used in key generation.
7. Partially Encrypted File Carving and Reconstruction
-
Summary: Some ransomware only encrypts file headers or partial contents to speed up the process, leaving data recoverable.
-
Technical Recovery: We use forensic carving tools with custom file type definitions to extract unencrypted portions. For database files, we repair header structures and rebuild table indexes. For video files, we reconstruct container formats (MP4 moov atoms, AVI headers) to make files playable despite partial encryption.
8. Temporary File and Cache Recovery
-
Summary: Applications create temporary copies and caches that may escape encryption.
-
Technical Recovery: We conduct deep scans of temporary directories and application-specific caches. For Microsoft Office, we recover .tmp and .asd files. For Adobe applications, we extract recovery data from .pek and .pmk files. We also analyze browser caches and system restore points for unaffected file versions.
9. Negotiation with Attackers as Intermediary
-
Summary: When technical decryption fails, engaging with threat actors may be the only option to obtain decryption keys.
-
Technical Recovery: We act as professional intermediaries using Tor-based communication channels. We verify attacker key possession by sending specially crafted test files for decryption. Our negotiation team employs psychological tactics and payment structuring to reduce ransom demands by 40-70% on average while managing cryptocurrency transactions through secure, monitored wallets.
10. Flawed Encryption Algorithm Implementation Analysis
-
Summary: Ransomware authors often implement strong algorithms incorrectly, introducing vulnerabilities.
-
Technical Recovery: We analyze encrypted output patterns to identify implementation flaws. For static IV usage, we perform known plaintext attacks. For ECB mode misuse, we identify patterns that reveal file structure. For weak key scheduling, we exploit related-key attacks to reduce effective key strength.
11. Master Decryption Key Leakage Analysis
-
Summary: Programming errors sometimes cause master decryption keys to be embedded in binaries or leaked in network traffic.
-
Technical Recovery: We perform static analysis on ransomware executables using FLOSS (FireEye Labs Obfuscated String Solver) to extract obfuscated strings. We also analyze network packet captures for key material exfiltration, using Wireshark with custom dissection plugins to identify cryptographic data in C2 communications.
12. Database Log Replay for Consistent Recovery
-
Summary: Database management systems maintain transaction logs that can restore data to pre-infection states.
-
Technical Recovery: We take encrypted database files and corresponding transaction logs, then use native database tools to restore to a point before infection. For SQL Server, we use LOG shipping and point-in-time recovery. For Oracle, we apply archived redo logs up to the second before encryption began.
13. Email Attachment and Cloud Sync Recovery
-
Summary: Files recently emailed or synced to cloud services may exist in unencrypted form on servers.
-
Technical Recovery: We work with IT administrators to access email server archives and cloud version histories. For Office 365, we utilize the 14-day version history and retention policies. For Google Workspace, we access native versioning and trash recovery features to restore pre-encryption file states.
14. Firmware-Level Ransomware Mitigation and Recovery
-
Summary: Sophisticated ransomware (RobbinHood) targets MBR/GPT to prevent booting.
-
Technical Recovery: We use hardware write-blockers to image drives, then manually repair damaged boot sectors using disk editors. For GPT corruption, we reconstruct the partition table using backup GPT headers typically stored at the disk’s end. We validate repairs using checksum verification of critical structures.
15. Entropy Analysis to Identify Encryption Scope
-
Summary: Encrypted data exhibits high, uniform entropy compared to normal file patterns.
-
Technical Recovery: We use Binwalk and custom Python scripts with scipy.stats.entropy to calculate Shannon entropy of every sector. By plotting entropy distributions, we visually identify encrypted regions and isolate them for targeted recovery efforts, focusing resources on unaffected areas.
16. Ransomware Bug Exploitation and Logic Bomb Analysis
-
Summary: Some ransomware contains “logic bombs” or time-based triggers that can be exploited.
-
Technical Recovery: We analyze ransomware in controlled sandboxes, monitoring API calls for time-based functions. By manipulating system clocks and environmental factors, we trigger failsafes or disable encryption routines. For time-locked ransomware, we identify and exploit race conditions in the encryption process.
17. File System Journal ($UsnJrnl) Forensic Analysis
-
Summary: The NTFS USN Journal logs all file changes, providing a timeline of ransomware activity.
-
Technical Recovery: We parse the $Extend$UsnJrnl using analyzeMFT and custom tools to reconstruct the attack timeline. The journal provides original file names, paths, and timestamps before encryption, enabling precise recovery targeting and validation of restored data integrity.
18. Hybrid Encryption Attack Focusing on Weakest Link
-
Summary: Ransomware uses hybrid encryption where weak points exist in the cryptographic chain.
-
Technical Recovery: We focus attacks on the weakest cryptographic component. For RSA-512 implementations, we perform GNFS factorization. For weak ECC implementations, we use Pollard’s rho or baby-step giant-step algorithms. For poorly implemented symmetric encryption, we employ slide attacks and related-key techniques.
19. Bootkit and MBR Ransomware Removal and Data Reconstruction
-
Summary: Ransomware like Petya encrypts the Master File Table and overwrites the MBR.
-
Technical Recovery: We create sector-by-sector images, then locate and rebuild the backup MFT (typically near the volume’s middle). We repair or replace malicious MBR code with standard boot sectors, restoring file system access to then target encrypted user files with appropriate decryption methods.
20. Side-Channel Attack on Encryption Process
-
Summary: Analyzing system behavior during encryption can reveal information about cryptographic keys.
-
Technical Recovery: In controlled environments, we monitor power consumption, electromagnetic emissions, and cache timings during ransomware execution. Using Differential Power Analysis (DPA) and Correlation Power Analysis (CPA), we correlate physical measurements with cryptographic operations to statistically derive key material.
21. Decoy File Entrapment and Known Plaintext Attacks
-
Summary: Strategic placement of decoy files with known content enables powerful cryptanalytic attacks.
-
Technical Recovery: We pre-seed systems with high-entropy files of specific sizes and checksums. When encrypted, these provide perfect known plaintext-ciphertext pairs. We XOR these pairs to derive keystreams or directly attack encryption parameters, significantly reducing the complexity of key recovery.
22. Ransomware-as-a-Service (RaaS) Infrastructure Takedown Collaboration
-
Summary: Collaborating with law enforcement to dismantle RaaS operations can yield master decryption keys.
-
Technical Recovery: We work with international law enforcement (NCA, FBI, Europol) to analyze C2 server communications and identify infrastructure. During takedowns of operations like Hive and REvil, we help extract master decryption keys from seized servers and integrate them into our decryption tools.
23. Process Hollowing and Code Injection Analysis
-
Summary: Ransomware injects malicious code into legitimate processes to evade detection.
-
Technical Recovery: We use kernel-level debuggers (WinDbg) to attach to suspicious processes without crashing them. We dump process memory and scan for injected code sections using entropy analysis and signature detection. Within these injected code regions, we often find encryption routines and active key material.
24. Custom Decryptor Development for Novel Strains
-
Summary: New or obscure ransomware strains require development of proprietary decryption tools.
-
Technical Recovery: We reverse-engineer ransomware binaries using IDA Pro and x64dbg, mapping encryption routines and key handling. We then develop C++ or Python decryption scripts that implement the inverse operations. These tools are added to our continuous integration pipeline for automated testing and refinement.
25. Forensic Imaging and Isolated Analysis Protocol
-
Summary: Foundational forensic imaging ensures evidence preservation and prevents further damage.
-
Technical Recovery: We connect affected storage to Tableau TX1 forensic write-blockers and create raw (dd) images with simultaneous E01 verification. All hashing uses SHA-256 with sequential verification throughout the recovery process. Analysis occurs on isolated networks with air-gapped systems to prevent ransomware spread or C2 communication.
Advanced Technical Capabilities
Cryptographic Attack Infrastructure:
-
8x NVIDIA RTX 4090 GPU array for brute-force attacks
-
64-core AMD EPYC server cluster for factorization
-
Custom OpenCL/CUDA kernels for cryptographic optimization
-
Distributed computing network for large-scale attacks
Forensic Analysis Expertise:
-
Memory analysis with custom Volatility plugins
-
File system journal and metadata reconstruction
-
Network traffic analysis with custom dissection
-
Malware behavioral analysis in controlled sandboxes
Reverse Engineering Capabilities:
-
Advanced static and dynamic analysis
-
Code deobfuscation and unpacking
-
Cryptographic algorithm identification
-
Vulnerability discovery in ransomware implementations
Why Choose Swindon Data Recovery for Ransomware?
-
25 Years of Cybersecurity Expertise: Deep knowledge of evolving ransomware tactics and countermeasures
-
UK’s Largest Ransomware Database: Comprehensive collection of signatures, decryptors, and attack vectors
-
Advanced Cryptographic Infrastructure: State-of-the-art computing resources for breaking encryption
-
Law Enforcement Collaboration: Active partnerships with national and international cybercrime units
-
Free Comprehensive Diagnostics: Detailed technical assessment with transparent pricing
-
Success-Based Pricing: Payment only after successful data recovery
Contact Swindon Data Recovery today for a free, confidential forensic evaluation of your ransomware-infected systems. Experience the difference that 25 years of cryptographic expertise makes in recovering your encrypted data. Do not pay the ransom until you have consulted with the UK’s leading ransomware recovery specialists.